Gone are the days of digital euphoria, where thought leaders pontificated on the ways in which the internet and global connectivity would unite the world and foster a new era of world peace and prosperity. With speculation...
KEEP READINGThe CPD Blog is intended to stimulate dialog among scholars and practitioners from around the world in the public diplomacy sphere. The opinions represented here are the authors' own and do not necessarily reflect CPD's views. For blogger guidelines, click here.

The New Netwar: A Data-Driven Response
Jihadist use of the internet to distribute information and multimedia content is closely aligned with John Arquilla and David Ronfeldt’s concept of “Netwar:” jihadists’ leaderless, yet “networked organizational structure” and ideas of emergent behavior in complex systems.
As the use of the internet has grown, so extremists have utilized the opportunity it creates. The recent report: The New Netwar presents significant new data on internet use by jihadist groups. The report shows that for those charged with countering the media mujahideen online, strategy cannot be built on a severely limited view of ISIS production nor the latest catchphrase and analytical fad, such as the current distraction of a cyber-centric “Virtual Caliphate."
In my article for Perspectives on Terrorism, the "Swarmcast" is demarcated by its speed, agility and resilience. Swarmcast has been used by ISIS since 2014. As predicted then and as is evident now, the nature of the mobile-enabled Swarmcast means that it can appear to be degraded, but it has really only been reconfigured.
Three years on, despite much hype and commentary about a purported decline in ISIS content, the data in The New Netwar confirms the 2014 prediction and shows that the decline of ISIS in the online space has been significantly overstated.
Production
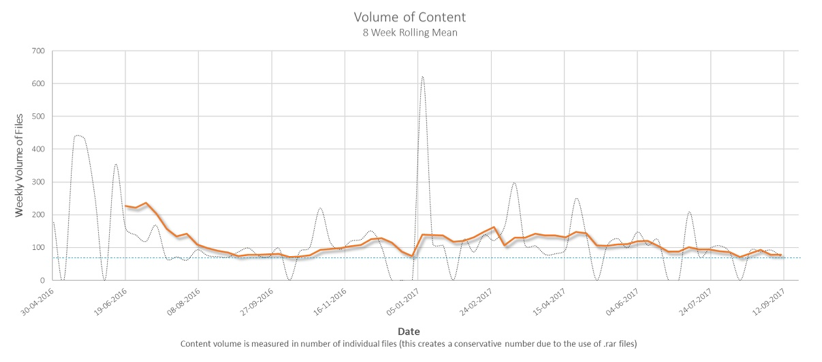
Despite fluctuations in weekly production and research claiming a “huge and steady decrease” or 30% to 40 % reduction, levels have remained relatively consistent. The data presented in The New Netwar report shows production was at a similar level a year ago.
Equally, the detailed weekly analysis in The New Netwar highlights that the conservative figure for recorded weekly production dwarfs previous estimates of monthly visual production reported by CTC. Some of the reason for the difference between contemporary commentary and the data on media production in The New Netwar is related to methodological issues, questionable sampling and poor understanding of data science, which contributes to impression of decline. As a result, some studies are little more than a measure of the authors’ ability to find content rather than accurate measures or analysis of production by ISIS.
Doubling Down on Decline
In addition to casting doubt on claims of a major decline in content production, the report also challenges the sense amongst researchers and commentators that the fight has been largely won on Twitter, with ISIS seeing diminishing returns. For example, the findings of a UK Home Office-funded research project produced by VOX-Pol that stated, “the IS Twitter community is now almost non-existent.” Yet as The New Netwar demonstrates, the reality is not as rosy as this Micawberish verdict.
Naturally, as the media mujahideen embrace the greater utility of other platforms, such as the shift to Telegram, there has been a corresponding drop in the portion of ISIS traffic on Twitter which is intended to galvanize the mujaheen vanguard. However, The New Netwar says the shift to the greater security and utility of Telegram should not be misinterpreted as a decline in the group itself. Furthermore, the impression of decline in the use of Twitter may also occur because researchers are less successful at locating the content on Twitter than they once were.
To test this second perspective, The New Netwar provides an analysis of shortlink data from URLs which lead to ISIS content, using a similar time period as the VOX-Pol study. For clicks where the referring platform was detected by the shortlink provider, the results are telling – and cast significant doubt on research claiming that ISIS has struggled to use Twitter. The graph in the report highlights the breadth of the ecosystem, and this version highlights that Twitter still has a prominent role in distributing content.
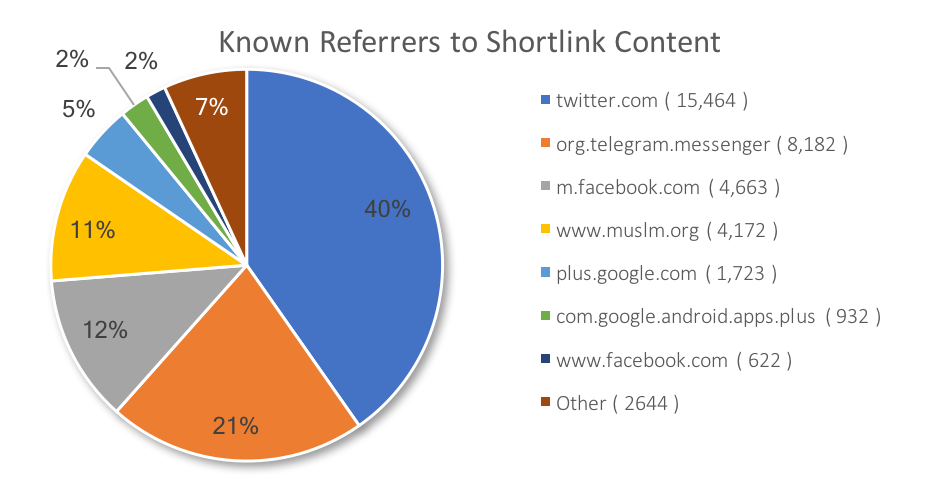
It is very difficult to square the claims that ISIS’ use of Twitter is “vanishingly small” or “virtually non-existent” with the proportion of known traffic coming from the platform.
Not so fast...
Shortlinks are a useful indicator of the relative proportion of traffic from different platforms, given that data for other links are unavailable. However, the data comes with caveats, including those listed in the report and also discussed here. In The New Netwar data, content is predominantly produced by Amaq and is a particular type of ISIS content, but this does not affect the finding that ISIS is still able to distribute content through Twitter.
Similarly, the use of a VPN can disguise the origin of traffic. While it is easy to claim many Jihadi sympathizers use a VPN (if you do not feel need to provide evidence), there are a number of reasons to believe the level of distortion of known clicks caused by a VPN is low. Each is a good reason individually and collectively they are persuasive:
- First, while Jihadist channels often encourage users adopt a VPN, the frequency with which this is mentioned in Jihadist channels (including reports by مؤسسة افاق الإلكترونية Electronic Horizons Media Foundation) indicates Jihadists, at least, do not believe their counterparts are actually using them; otherwise regular entreaties to use a VPN would be redundant.
- Second, the location data available for shortlinks highlights locations extremely unlikely to be selected for VPN nodes. Given a choice of VPN servers globally, it is unlikely a user would look for a server in Turkey, Saudi Arabia, Yemen, Iraq, Egypt or Algeria given the potential limitations caused by content filtering and bandwidth. Yet these are all in the top 10 locations and have active Jihadist groups - some with significant operational capability.
- Third, humans huddle. Once ISIS sanctioned Telegram as their core communication channel with supporters, the role of focal points (or Schelling points) became an important reason why users migrated to certain platforms rather than any specific feature, including the security of Telegram which attracted early adopters.
- Finally, as the data shows over 50% of known referrers come from Twitter or Facebook, arguments about security-aware Telegram users distorting data by operating VPNs are misplaced.
Mismatch
Even when the caveats are considered, there remains an immediately evident mismatch between the data and the claims made by those commentators doubling down on decline.
If such claims were accurate, one would not expect Twitter to outstrip Telegram and Facebook as the top referrer to ISIS content. Yet for these shortlinks, gathered during the same timeframe as the Home Office funded VOX-Pol study, Twitter was the top access point for known referrers.
During the research, two simple truths emerged:
1. Just because researchers cannot find content on Twitter does not mean the jihadist movement is in decline.
2. Just because researchers cannot find content on Twitter does not even mean ISIS is unable to utilize Twitter. Data clearly shows that ISIS continues to drive traffic to their content via Twitter, but it seems many researchers are simply unable to locate it.
The data in this post is available in greater detail in “'Swarmcast’: the Use of the Internet by the Jihadist Movement” in Part 1 of The New Netwar: Countering Extremism Online published by Policy Exchange on September 18, 2017.
Photo by CafeCredit.com I CC BY 2.0
Visit CPD's Online Library
Explore CPD's vast online database featuring the latest books, articles, speeches and information on international organizations dedicated to public diplomacy.
POPULAR ARTICLES
-
January 29
-
January 20
-
January 28
-
February 6
-
January 8
Join the Conversation
Interested in contributing to the CPD Blog? We welcome your posts. Read our guidelines and find out how you can submit blogs and photo essays >.